Why Continuous Attack Surface Management is No Longer Optional

Who Needs Attack Surface Visibility?
From Executive Orders to cyber insurance and evolving regulations, security teams are entering the age of evidence. Want to do business with a government entity? You must demonstrate adherence to zero-trust principles. Want cyber insurance? You need documentation of your entire attack surface. Want to conduct financial services business in various regions? Show your operational resiliency. Whether it is the Board, C-Suite, or government regulators, security teams are being asked to demonstrate proper visibility and control over all enterprise assets and data, AKA their attack surface.
The Expanding Attack Surface Challenge
For most enterprises, their online presence continues to grow in scale and complexity—often beyond the oversight or control of security teams. As an enterprise partner to scale and accelerate business outcomes, every digital migration, web service, and remote access adds to the attack surface. These growth initiatives provide many opportunities for businesses and the cybercriminals who target them. This is one reason why attack surface expansion was identified by Gartner as a top risk and security trend for 2022.
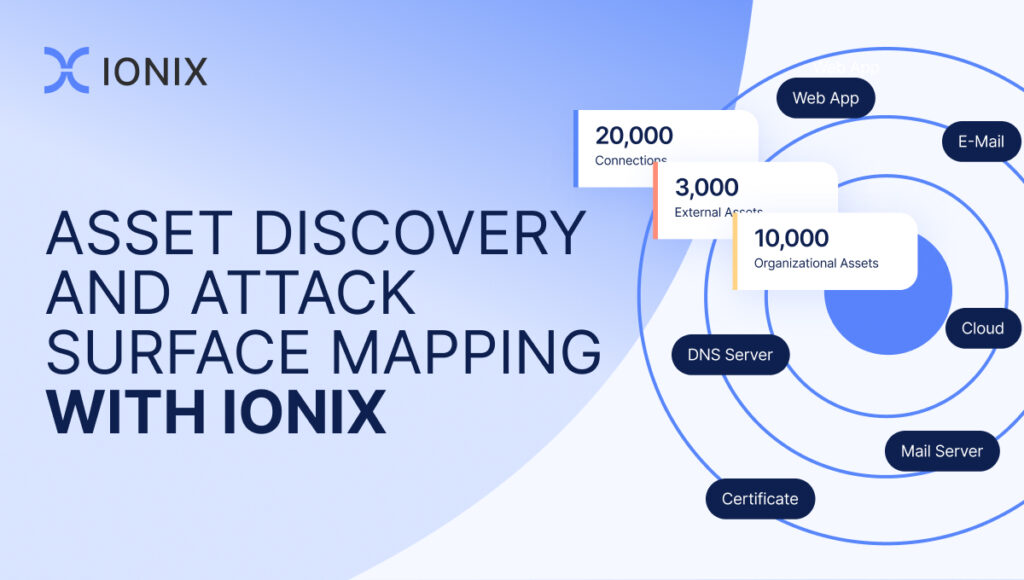
Having an updated, complete view of the attack surface is the critical first step in evaluating the organization’s risk profile. Security teams need complete visibility of this sprawling attack surface, including every dependency, connection, and vulnerability across all public-facing assets. This challenge is compounded in the ways:
First, the fact that the attack surface risk extends beyond every internet-facing asset to its connected digital supply chain. Simply put, if a 3rd, 4th or 5th party asset you’re connected to is at risk, so are you.
Second, the modern attack surface is dynamic. Every business action and interaction that your organization and your business partners make changes the assets and the associated risk.
Third, the threat landscape is constantly changing as well. Being prepared to act quickly is essential.
The Need for Continuous Attack Surface Discovery
Achieving visibility of the entire attack surface at the pace and complexity of enterprise business requires a robust attack surface management platform that provides fully automated, continuous attack surface discovery of all of your internet-facing assets and their connected digital supply chains.
The ASM platform should continuously monitor PKI, DNS, and Internet Indexes to identify additions and reductions in your attack surface. Achieving this with complete coverage and high precision requires advanced technologies like machine learning models, which have been optimized for your enterprise. Many solutions on the market are limited in their ability to identify organizational assets. Even more, solutions are unable to effectively weed out false positives. As a result, security teams continue to operate in the dark while wasting precious time sifting through irrelevant noise.
Automated Risk Assessment and Prioritization
In addition to continuous discovery, automated contextual risk assessment for every asset provides lean security teams with visibility and control – so they can effectively keep pace with their vast and dynamic IT environments and the evolving threat landscape. By prioritizing the most critical vulnerabilities first, security teams know exactly where to start. Actionable insights and detailed evidence enable teams to mitigate risk effectively by quickly eliminating attack vectors and proactively preventing breaches.
To see the unmatched coverage and precision provided by our ML-based continuous attack surface discovery, book your demo.