- Platform
- Solutions
- Expose and Manage ThreatsContinuously identify, expose and remediate critical threats
- Reduce Attack SurfaceThe roadmap to reducing your attack surface
- Control Subsidiary RiskManage cyber risk across all your subsidiaries
- Cloud Attack SurfaceClose Security Gaps Across Your Cloud Attack Surface
- Improve Security PostureReduce risk systematically
- Manage M&A riskEvaluate candidate’s cyber risk
- Learn
- Company
Threat Exposure Radar ExplainedSolutions - Exploitable vulnerabilities
- Critical misconfigurations
- Data exposures
Ionix Connective IntelligenceProductProduct Highlights
VALIDATE EXPOSURE ACROSS YOUR
ENTIRE ATTACK SURFACETest for external exposures, continuously
Identify exploitable vulnerabilities, critical misconfigurations and data exposures
Reduce false positives. Increase trust
Validate exposures to effectively collaborate with IT and accelerate remediation
Prioritize real-world risks
Go beyond CVEs and CVSS scores to prioritize what matters most
AUTOMATED EXPOSURE VALIDATION
Test for external exposures, continuously
Conduct active yet non-intrusive security tests that simulate external attacks, across your entire attack surface. Make exposure validation a continuous and integral part of your organization’s cybersecurity practice without disrupting operations.
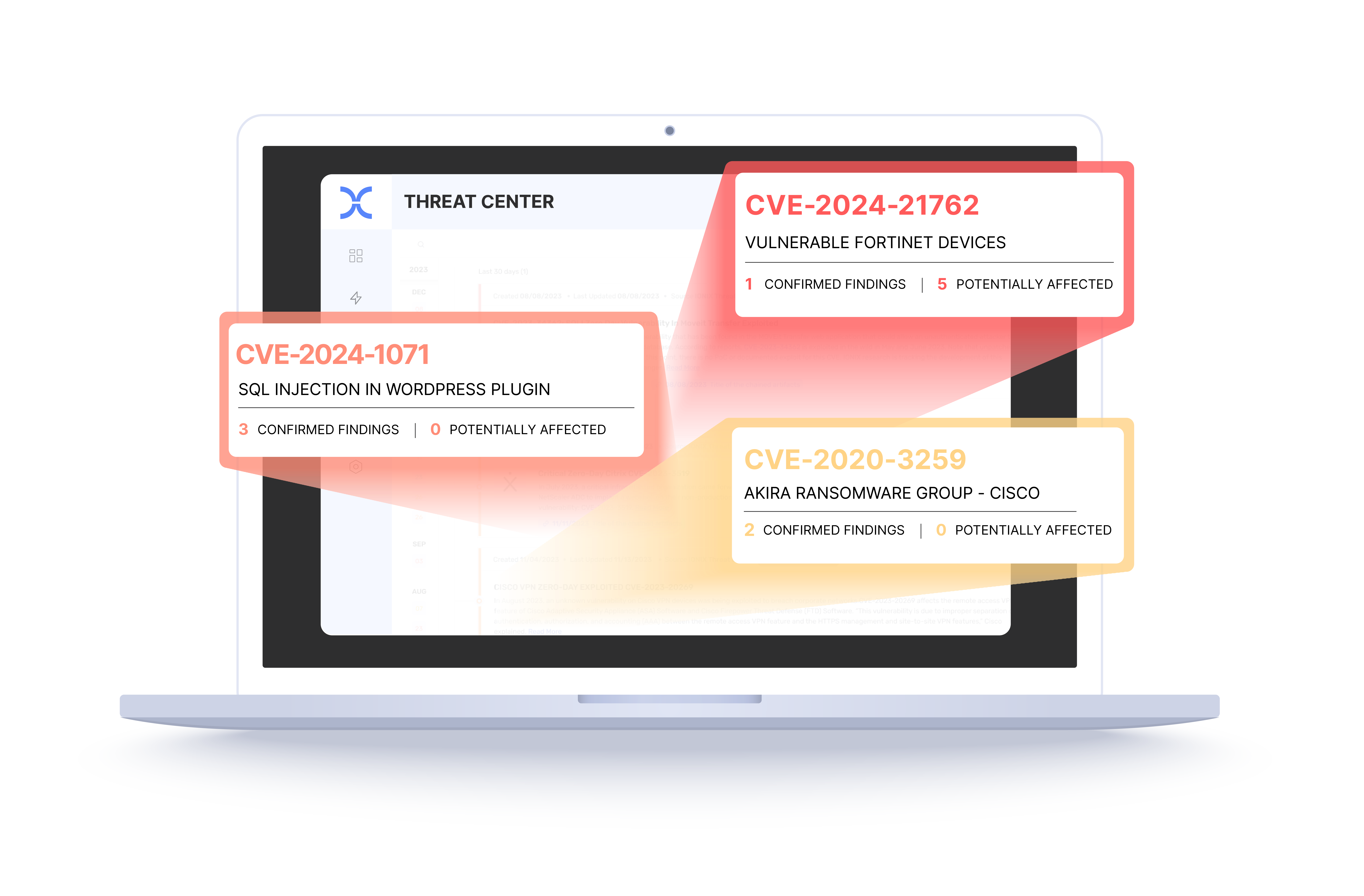
IONIX Exposure Validation tests for thousands of risks and continually expands coverage in response to emerging threats including:IONIX THREAT CENTER
Accelerate zero-day response
Gain clear visibility into your zero day attack surface exposures to effectively streamline remediation with IONIX Threat Center. Validate exploitable risks posed by the latest zero-day vulnerabilities that are exploited in the wild.
CYBER ATTACK SIMULATION
Reduce false positives. Gain trust.
False positive alerts are a waste time and resources. Even worse, they erode trust with IT stakeholders. With IONIX Security Validation, your security team can validate exploitable exposures and confidently collaborate with IT to accelerate remediation.
EXPLOITABILITY PRIORITIZATION
Prioritize real-world risks
Go beyond CVEs and CVSS scores with IONIX prioritization framework and security validation. With IONIX, your security teams can focus on what matters most by automatically exposing exploitable risks and gauging impact using our asset importance rankings.
- Solutions