- Platform
- Solutions
- Expose and Manage ThreatsContinuously identify, expose and remediate critical threats
- Reduce Attack SurfaceThe roadmap to reducing your attack surface
- Control Subsidiary RiskManage cyber risk across all your subsidiaries
- Cloud Attack SurfaceClose Security Gaps Across Your Cloud Attack Surface
- Improve Security PostureReduce risk systematically
- Manage M&A riskEvaluate candidate’s cyber risk
- Learn
- Company
Threat Exposure Radar ExplainedSolutions
Ionix Connective IntelligenceProductCloud security operations
CLOSE SECURITY GAPS ACROSS
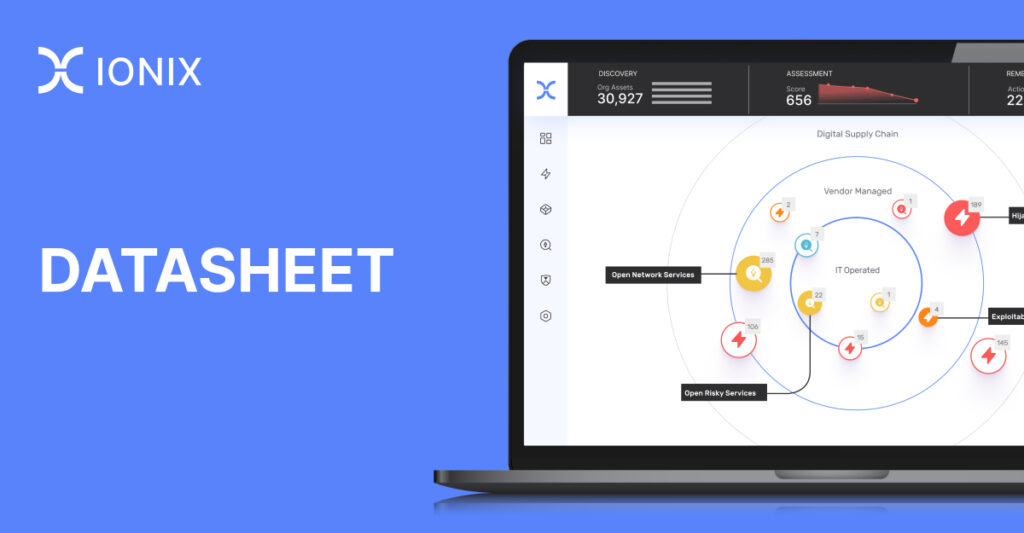
YOUR CLOUD ATTACK SURFACEDiscover your cloud attack surface and digital supply chain from the
attackers’ perspective. Prioritize risks and validate exposures to identify
and fix what matters most, faster.Cloud Security Operations
Secure Your Cloud Attack Surface and Digital Supply Chain
In today’s complex digital landscape, traditional security approaches are often inadequate, leaving significant gaps in your cloud security posture. IONIX’s cloud security solution, ‘Cloud Cross-View’ overcomes the limitations of CSPM with external visibility that surfaces Shadow IT, unintentional internet exposures, and digital supply chain risks. With read-only integration into public cloud environments including AWS, GCP, and Azure, IONIX Cloud Cross-View offers a holistic view across all your environments from an attacker’s perspective.
IONIX Cloud Cross-View
Bridge Security Gaps From the Attacker’s Perspecitve
Manage external risks and exposures across your interconnected hybrid cloud and on-premises environments.
Unified Hybrid Environment View: Gain unmatched visibility into your cloud attack surface and digital supply chains with IONIX Cloud Cross-View.
Prioritize with Connective Intelligence: Map attack paths from external assets and across cloud environments that put critical assets at risk.
Validate Exposures: With IONIX Exposure Validation, test exploitability using non-intrusive methods to surface real-world exploitable risks without disrupting your operations.
Exposure Validation
Validate External Exposures Across Clouds
With Cloud Cross View, IONIX extends its Exposure Validation conducting non-intrusive exploitability testing to pinpoint real-world exposures across your public cloud environments. This validation process is crucial for effectively prioritizing and accelerating remediation of exploitable risks, effectively reducing the organization’s overall exposure to potential attacks.
REQUEST AN ATTACK SURFACE SCAN TODAY
Discover the full extent of your online exposure so you can protect it.
- Solutions