CVE-2024-24919 – Check Point Quantum Gateway

CVE-2024-24919 is a critical security vulnerability identified in Check Point Quantum Security Gateway, a widely used network security appliance. This vulnerability allows attackers to exploit the gateway, leading to the exposure of sensitive information. As a zero-day exploit, it presents significant risks to organizations relying on Check Point for their network security.
Details of the Vulnerability
According to the National Vulnerability Database (NVD), CVE-2024-24919 affects the VPN component of the Check Point Security Gateway. This vulnerability stems from improper handling of sensitive data within the VPN gateway, which can be exploited to leak confidential information such as credentials and internal network details.
The European Union Agency for Cybersecurity (ENISA) highlighted that this flaw can be triggered remotely by unauthenticated attackers, making it particularly dangerous as it can be exploited over the internet without requiring physical access to the affected systems.
Updates – May 30
On May 27, Check Point announced, and then updated a security alert on CVE-2024-24919 related to internet-connected Quantum Security Gateways. The post added details on impacted Gateways – those which have been configured with IPSec VPN, remote access VPN or mobile access software blade. According to the advisory, on May 30 Check Point confirmed exploitation in the wild. The exploit was identified on devices configured with local accounts using password-only authentication. Check Point elaborated that the ongoing exploitation attempts stem from a previously undisclosed vulnerability, underscoring the urgency of taking swift measures to safeguard against it.
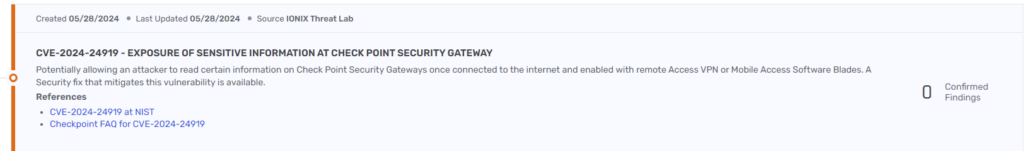
This zero-day vulnerability potentially allows an attacker to read certain information on Check Point Security Gateways once connected to the internet and enabled with remote Access VPN or Mobile Access Software Blades. A security fix that mitigates this vulnerability is available.
Follow the instructions to deploy the Security Gateway hotfix here:
https://support.checkpoint.com/results/sk/sk182336
IONIX customer can review the assets impacted by CVE-2024-24919 in our Threat Center.
Check Point recommends protecting yourself by following the instructions here. Fixes include:
- Installing a mandatory Security Gateway Hotfix to prevent exploit of CVE-2024-24919
- Changing the password of the LDAP account unit
- Resetting password of local accounts connecting to VPN with password authentication
- Renewing Security Gateway’s Inbound SSL Inspection server certficates
- Renewing Security Gateway’s Outbound SSL Inspection CA certificate
- Resetting Gaia OS passwords for all local users
Actions for IONIX Customers
For IONIX customers, who are receiving a complete view of their external attack surface, CVE-2024-24919 details are available in our Threat Center – this helps to understand if any related assets in your infrastructure have been exploited. IONIX Security Research Team developed a payload to validate for our customers’ specific Check Point gateways that are exploitable. IONIX also offers a free scan to those wishing to check for their exploitable assets.
Security teams face a critical task: identifying the presence and locations of Check Point Quantum Security Gateways within their organization. These vulnerable assets, constitute a part of the external attack surface. It’s imperative for security organizations to broaden their scope beyond assets directly managed by IT. They must acknowledge that vulnerable assets could also be dispersed within subsidiaries, recently acquired firms, or satellite offices, potentially operating under diverse accounts. These complexities underscore the challenge of obtaining a comprehensive and precise overview of the entire asset inventory. Reach out to IONIX to schedule a demo of our Attack Surface Management platform and gain both deep discovery of all external-facing assets as well as exploit validation.