What Is An Online Ecosystem?

The Days of Monolithic Webservers are Long Gone
Practically any public webpage now loads multiple pieces of content, from multiple sources. In fact it’s now not uncommon to find webpages that have the browser open connections to dozens or even hundreds of different hosts in order to load all the objects of a single page.
One of the reasons webpages load multiple objects is the adoption of a service oriented architecture, with different microservices serving different types of content, but the main driver for this explosion of connections is the need to embed sites cookies and user trackers, site monitoring and analytics tools, social media plugins, and often advertising. Couple this with the emergence of Content Delivery Networks (CDNs), and the picture emerges of an ecosystem, with a large group of nodes that collectively serve each website, where many of the nodes are operated by 3rd party partners and vendors rather than the owner of the website.
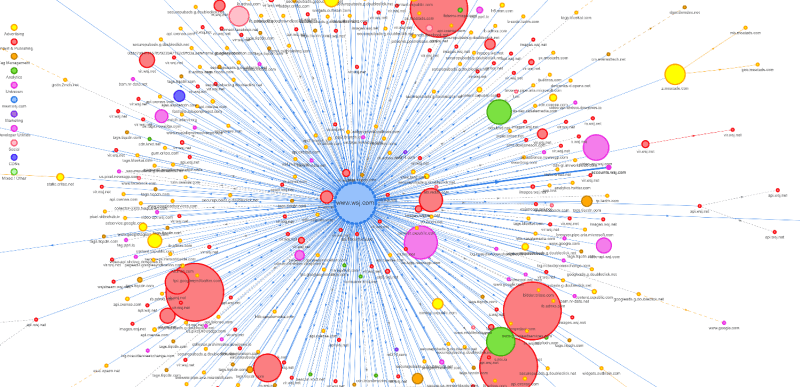
Technically, what generates this online ecosystem are, to begin with, HTML tags referencing other resources. One can start from the mostly innocuous ‘a’ tags used for hyperlinks, and go through the list of a dozen or so other tags that may be used to reference scripts, fonts, images, applets, iframes and ajax objects, among others.
HTML Tags Are Not the Only Generators of the Online Ecosystem
HTTP redirects also direct browsers to open a connection with a new FQDN in the context of loading a page, and so ecosystems should account for them as well. Similarly, DNS CNAME records involved in the resolutions of any of the domains referenced, are themselves ecosystem generators. More generally, any FQDN referenced by a DNS record for an organization’s domain is part of that organization’s online ecosystem.
As a first approximation, an organization’s ecosystem starts from
- Organization’s own set of 1st party assets
- Connections – HTML tags, HTTP redirects, DNS records, etc – to include all the assets that are referenced there.
References to Other Objects
Now, iframes and scripts, for instance, can and often do reference other objects as well, and e.g., DNS CNAME records can also form a chain. Similarly applets can refer to resources in additional sources in code. These chains can stretch quite far. A chain of 10 or 20 redirects, for instance, in not uncommon. So we see how an organization’s ecosystem is itself is “deep”, many layered, and as such not, in general, controlled by the organization whose ecosystem it is.
IT and Cyber Security Teams Shy Away From Taking Ownership of These Ecosystems
In most cases, IT and Cyber security teams are quite blind to the ecosystems’ existence: In general, there are no direct network connections between 1st and 3rd party assets in the ecosystem– the model for this ecosystem is “meet me at my end-users browsers and apps” – and so perimeter security tools, WAFs and firewalls, data center proxies and URL filtering solutions, simply do not “see” the ecosystem, let alone offer any protection. Nor has there been any alternatives. Security and governance teams have been struggling to get the tools in house that discover their own 1st party assets, but none has offered them ecosystem visibility. And so, these security teams did not concern themselves with overseeing, let alone securing the ecosystem.
Attackers Have Found the Online Ecosystem an Attractive Conduit for Exploits
A deep-dive into the risks posed by subsidiaries vulnerabilities and their potential misconfiguration is beyond the scope of this blogpost, but I’m sure that you, the reader, can appreciate the risks a 3rd party host poses to your organization, if your websites use it for loading scripts. If someone could hack that host and manipulate the script, they’d be able to harvest your users’ credentials and data, as well as manipulate the data that they might enter into your system. There have been many attacks that happened that way.
Thus, the time has come for a platform for a system that generalizes attack surface discovery and makes the whole online ecosystem visible. Furthermore the system should scan the whole ecosystem and assess the risks posed by each and every one of these ecosystem connections, across all your assets. This is what we do at IONIX.




