
Comprehensive Visibility
Gain complete visibility into all your organization’s exposed assets and risky connections – deep into your vendor managed assets and infrastructure dependencies.
Learn More



Reduce external exposure by addressing high-impact exploitable vulnerabilities.
IONIX provides full external attack surface visibility – deep into your digital supply chain risks – then pinpoints and validates exploits and streamlines remediation. Teams with IONIX work more efficiently, spend less time chasing noise and ultimately reduce MTTR.

Gain complete visibility into all your organization’s exposed assets and risky connections – deep into your vendor managed assets and infrastructure dependencies.
Learn More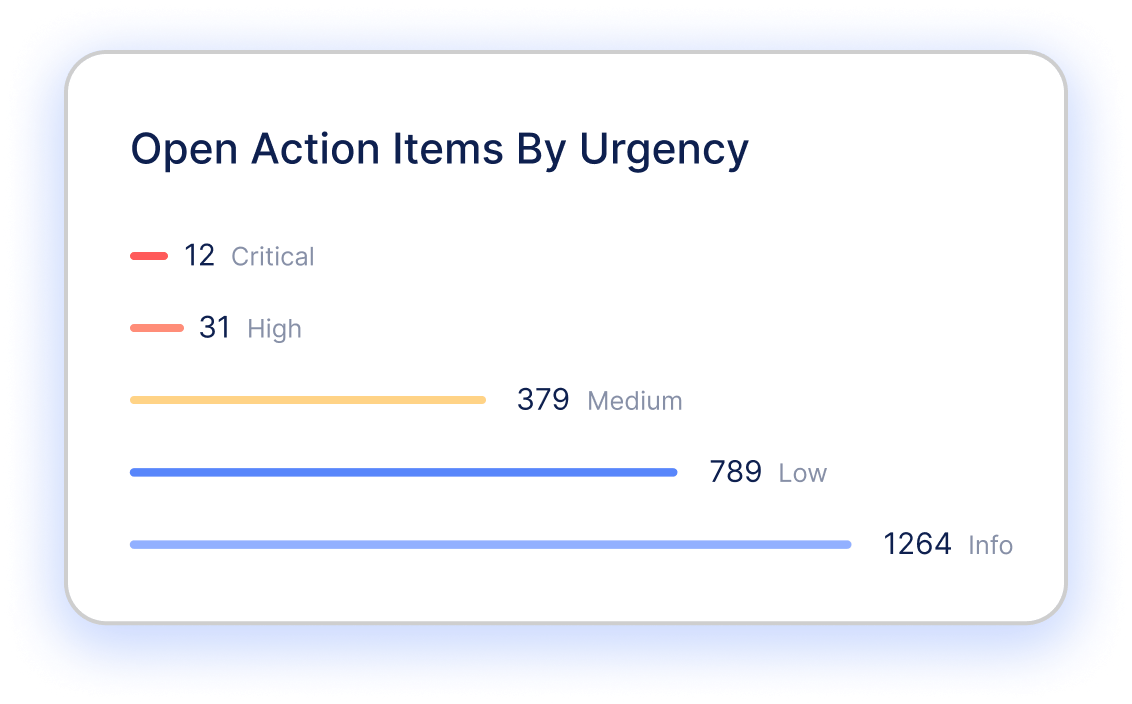
Focus on what needs to be addressed today – based on blast radius, exploitability, and threat intelligence.
Learn More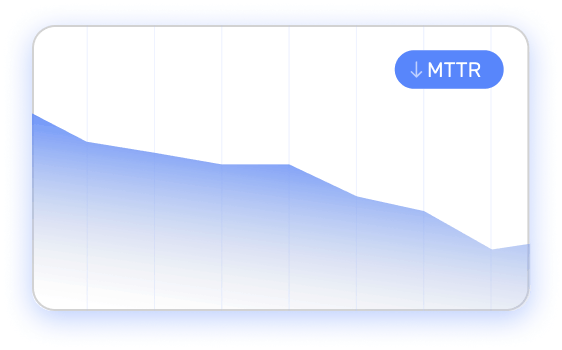
Accelerate risk resolution with clear action items and integrated workflows across teams and gain automatic risk mitigation with IONIX Active Protection.
Learn MoreDiscovery and mapping of all external assets including vendor-managed and digital dependencies.
Analysis to determine asset types and software running, correlating with NVD data.
Examination of security dimensions, IT hygiene, open ports, misconfigurations, etc.
Perform non-intrusive security tests, validating actual exposures.
Prioritize validated risks using clustering based on choke points, assets and teams.
Streamline validated findings to the right teams, integrations reduce MTTR and risk.
”Exceptional Service And Reliability Shout Out To Our Rep ForOutstanding Support! ”
IT Security & Risk Management Associate IT services
Learn More

”After working with IONIX for over a year, we are confident that its Ecosystem Security platform gives us the critical visibility we need to solve the difficult challenge of managing the risks and vulnerabilities in our entire digital supply chain.”
René Rindermann CISO, E.ON
Learn More
”Seamless Interface Simplifies Vulnerability Remediation”
CISO Manufacturing Company
Learn More

”It’s rare to find a cybersecurity solution that delivers almost immediate time to value with no impact on technical staffing. But that’s exactly what IONIX delivered.”
John Remo SVP Global Cloud / Infrastructure & Cybersecurity at WMG
Learn More
”IONIX Unveils Fresh Insights For Enhanced Attack Surface Visibility”
IT Security and Risk Management Security Architect
Learn More
””I favor IONIX over our previous solution because it offers significantly deeper visibility into findings and also covers a much larger portion of our network.””
IT Security Officer at a Retailer with 10,001+ Employees
Learn More
”IONIX: Seamless Integration, Precise Vulnerability Management,And Actionable Insights”
IT Security Officer Retail
Learn More

”IONIX provides us the strategic advantage of seeing our external attack surface, dynamically, in the same way attackers see it.”
Mike Manrod CISO, Grand Canyon Education
Learn More
”We ultimately chose IONIX because of its ability to go beyond vulnerability detection and into automatic active protection that mitigated the risk of hijacking any of the company’s domains”
CISO, Fortune 500
Learn More

Reduce MTTR by applying CTEM principles to your externally exposed assets. Find, validate and fix exploits fast.

Gain visibility into your real attack surface to systematically control and reduce attack surface sprawl

50% to 60% of all cyberattacks are being perpetrated via third parties. IONIX is the only ASM vendor addressing these kinds of attacks.
Expose your subsidiaries’ attack surface and digital supply chain risks – empowering local teams to improve their security posture

IONIX extends its unique Exposure Validation to the cloud – pinpointing real-world exposures across your cloud environments.
