Mastering Attack Surface Discovery: A Power Tool for Security Operations Pros

As security teams witness that their organization’s digital footprint keeps growing in size and complexity, the urgent need for attack surface discovery becomes clear. But what exactly does attack surface discovery entail, and why is it so crucial in today’s digital landscape? This blog post aims to demystify attack surface discovery and provide insights into its importance for security operations teams.
What is Attack Surface Discovery?
Attack surface discovery is the process of gaining visibility into an organization’s digital assets and their digital supply chains. It is the first and crucial step in Attack Surface Management since you cannot protect what you don’t know. Following the discovery step, potential vulnerabilities, misconfigurations, and security weaknesses are assessed, risks are prioritized, and remediation steps provided to SOC teams so they can better secure their organization’s digital landscape.
Attack Surface Expansion
In the rapidly evolving digital landscape, the expansion of the attack surface has become a significant concern for organizations worldwide. According to a recent ESG Security Hygiene and Posture Management survey, 62% of the organizations reported that their attack surface expanded over the past two years. This trend aligns with the top Gartner Security and Risk Management trend in 2022, highlighting the growing perils of Attack Surface Expansion. It is interesting to note that the same ESG survey reported that increased IT connections with third parties was the number one accelerant responsible for this expansion. This trend is expected to accelerate even more. As organizations continue to integrate more third-party services into their IT infrastructure, the attack surface inevitably grows through connected digital supply chains. This underscores the critical need for attack surface discovery.
Why Organizations Need Attack Surface Discovery?
According to the ESG Security Hygiene and Posture Management survey, enterprises conduce attack surface discovery for several reasons:
- Calculate risk and apply the right security controls
- Reduce risk of a ransomware attack
- Comply with regulatory requirements
- Complete asset inventory
- Keep up to date with frequently changing attack surface assets
- Secure the expanding attack surface
- Identify unknown assets that are vulnerable to cyber threats
- Identify low-priority assets that are exposed to malicious attack
The 2 Main Attack Surface Discovery Goals
While there are many underlying reasons for conducting attack surface discovery, the process itself has two essential goals:
Coverage: Eliminate false negatives and blind spots
The first goal of attack surface discovery is to eliminate blind spots and mitigate digital supply chain risks. In the context of cybersecurity, a blind spot refers to any area in an organization’s digital landscape that are unknown, ungoverned, such as Shadow IT and Zombie IT, which are often exposed to attacks. Shadow IT refers to IT systems, solutions, software, and services that are used within an organization without explicit organizational approval. Zombie IT, on the other hand, refers to IT resources that are no longer actively used or maintained, but are still connected to the organization’s network. These can include outdated systems, unused servers, or legacy applications that have been forgotten or overlooked.
Precision: Minimize noise and false positives
The second goal of attack surface discovery is to minimize false positives. False positives, in the context of asset discovery, refers to assets that are mistakenly flagged as belonging to the organization. False positives consume valuable resources and divert attention away from actual threats. Precise validation and attribution of assets to the organization is a critical capability that many ASM solutions fail to consistently achieve.
Automating Attack Surface Discovery
In the rapidly changing digital environment, automating attack surface discovery is becoming increasingly essential. According to the ESG survey, manual processes for attack surface discovery can take over 80 hours to complete, making them impractical and inefficient in the face of the scale and dynamism of modern digital landscapes. In this section we will take a deeper dive into the discovery automation process:
Types of assets
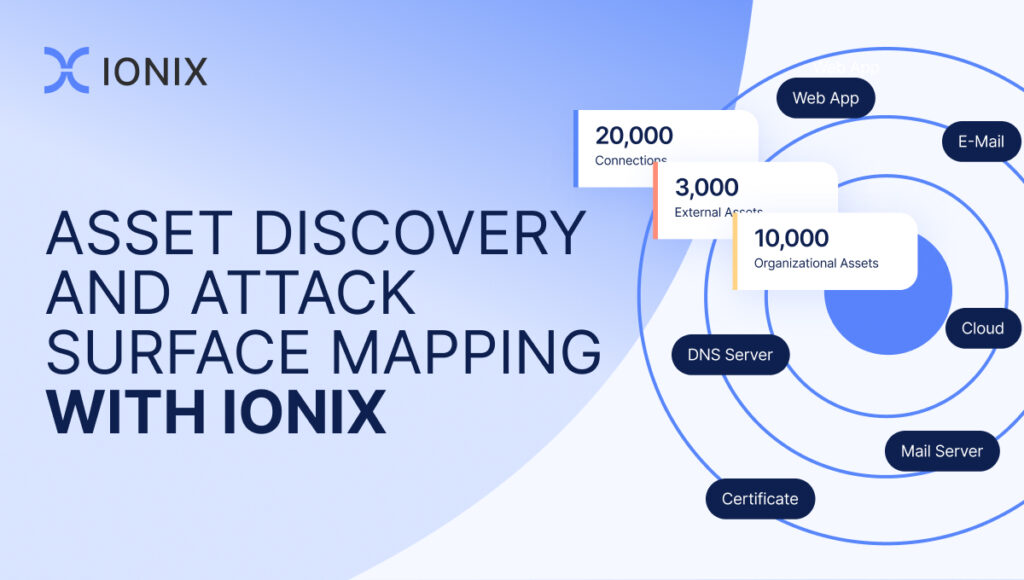
One of the key challenges in attack surface discovery is the sheer diversity and dynamism of the digital assets an organization may own or depend on. These can range from organizational domains and subdomains, IP addresses, cloud infrastructure, certificates, SaaS applications and managed platforms. Each of these asset types requires a different approach for effective discovery, underscoring the need for a diverse set of technologies and methods.
Attack surface discovery techniques
The diverse and dynamic nature of the modern attack surface mandates a multi-technique approach to attack surface discovery:
- Identify changes to your attack surface leveraging global event trackers to monitor public infrastructure such as domain registrars and global certificates.
- Use advanced AI algorithms and machine learning models to uncover all domains, subdomains, and IP addresses related to a network or system.
- Index the internet and public cloud platforms to identify and attribute all domains, IP blocks, and cloud infrastructure.
- Overlay continuous mapping to discover more organizational assets and generate a holistic graph of the entire attack surface across Web, Domain Name System (DNS), Cloud, Software-as-a-Service (SaaS), and On-Premises infrastructure.
In this context, attack surface discovery tools with advanced technologies like IONIX Connective Intelligence stand out. Leveraging this patent-based technology, IONIX is able to find 50% more assets than the competition. This significantly reduces the blind spots and noise in the attack surface discovery process, providing organizations with a more comprehensive and accurate view of their real attack surface.
Digital supply chains
The interconnected nature of today’s digital ecosystems means that an organization’s real attack surface extends beyond its own assets to include its digital supply chain. Here is why.
While organizations often focus on security the assets they own, threat actors don’t care about ownership. A threat actor set on penetrating your organization doesn’t care whether they’re attacking your internet-facing asset directly, or exploiting a vulnerability from a third-party digital service that provides a toehold into your environment.
Most Attack Surface Management solution limit their scope. IONIX Attack Surface Management platform extends discovery across the entire digital supply chain to the Nth connection.
Conclusion
The attack surface discovery process, which provides visibility into an organization’s digital assets, is the essential first step for identifying potential vulnerabilities and securing the digital landscape. As the integration of third-party services and the rapid evolution of digital technologies continue to expand the attack surface, a comprehensive, continuous and automated approach to attack surface discovery becomes increasingly necessary.
However, this process is not without its challenges. From eliminating blind spots such as Shadow IT and Zombie IT to minimizing false positives, maximizing the efficiency and effectiveness of attack surface discovery requires advanced technologies like IONIX Connective Intelligence. Furthermore, the interconnected nature of today’s digital ecosystems extends an organization’s attack surface to include its digital supply chains, emphasizing the need for a comprehensive approach to attack surface discovery. As we navigate this digital age, attack surface discovery remains a crucial component of effective cybersecurity strategy.
IONIX Attack Surface Discovery
IONIX is the attack surface management solution that discovers your real attack surface and its digital supply chain. Using IONIX Connective Intelligence, our attack surface discovery accurately discovers up to 50% more organizational assets than any other provider in the space, while minimizing the noise of false positives.
To see IONIX Discovery in action, Book a Demo.