Cyberpion is Now IONIX: Redefining Attack Surface Management with the Widest Coverage and Sharpest Focus

I’m thrilled to unveil our new identity: Cyberpion is now IONIX, a name that represents our radically different approach to protecting the modern attack surface and its digital supply chain. With IONIX, you’ll discover your organization’s real attack surface, including its sprawling network of asset dependencies – while separating the signal from the noise so your security team gains laser focus on your exploitable risks.
Read on to learn more about the core principles Cyberpion was founded on and how IONIX will continue to redefine attack surface management with the widest coverage and sharpest focus.
The Modern Attack Surface Requires a Different Approach
The world is changing.
The enterprise perimeter has gone from a closed, on-premises network to the cloud to its current state: a massively decentralized IT environment characterized by large-scale adoption of digital services – and an increasingly tangled digital supply chain.
And the stakes have never been higher as new threat actors emerge, exploiting increasingly sophisticated attack vectors to compromise organizations’ most critical assets.
But the tension facing cybersecurity leaders tasked with protecting their organizations is fundamentally the same as it’s always been. That’s the tradeoff between breadth and focus.
Breadth is an organization’s ability to identify the full range of relevant threats. Focus is an organization’s ability to address the most important and urgent threats. Breadth without focus means wasted money and resources. Focus without breadth means perilous blind spots.
The Cyberpion Insight Into Attack Surface Risk
Cyberpion (now IONIX) was founded on a unique insight into the nature of cybersecurity risk.
The idea is simple, but powerful. While analysts and cybersecurity leaders spend time classifying different types of organizational assets from the perspective of risk management – the reality is that this makes no difference to a threat actor.
A threat actor set on penetrating your organization doesn’t care whether they’re attacking your internet-facing asset directly, or exploiting a vulnerability from a third-party digital service that provides a toehold into your environment (e.g., a takeover of a dangling Azure blob called by an app referenced in a script on your website).
Cyberpion (now IONIX) was established on the premise that the increasingly interwoven nature of the digital supply chain demands a radically different approach to threat protection. It must identify the sprawling network of dependencies on the same level as an organization’s other assets – and separate signal from noise.
IONIX ASM: Secure Your Real Attack Surface
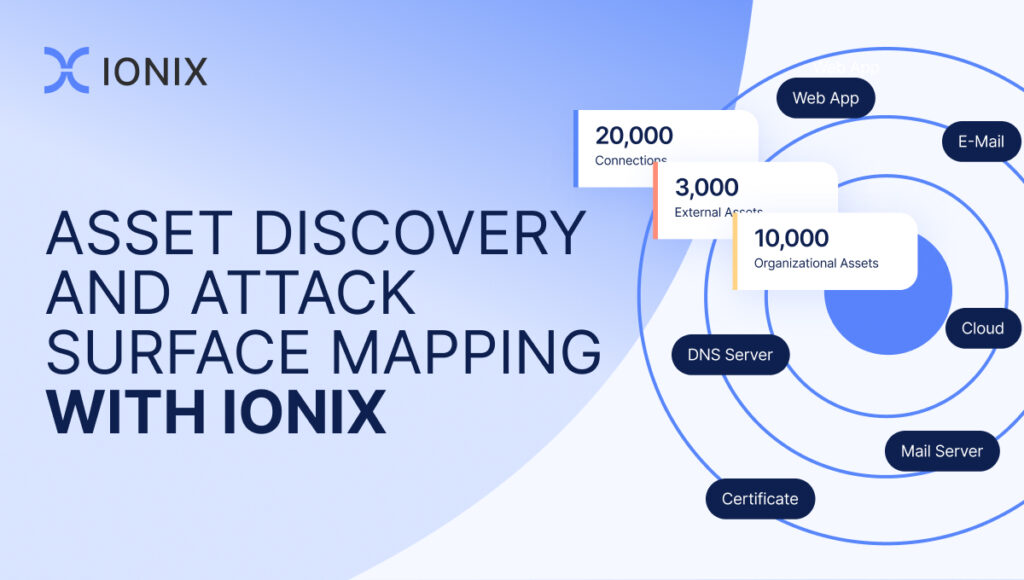
Using Connective Intelligence, IONIX ASM helps organizations take control of their real attack surface (a term defined in our glossary). IONIX not only covers the “real” attack surface, accurately discovering up to 50% more organizational assets than any other provider in the space and mapping your digital supply chain. It also provides unmatched tools for focusing on the real risks – exploitable vulnerabilities and misconfigurations with the biggest blast radius.
With IONIX, you can proactively prevent attacks before they happen, because we provide visibility into your unknowns and expose your most urgent, critical risks.
What’s in the Name?
IONIX (pronounced “eye on X”) is here to help you keep your eye on X.
But what is X? X is a target. It is your exposed asset, which cybercriminals can target to exploit.
Where IONIX (formerly Cyberpion) Goes from Here
External Attack Surface Management didn’t become a cybersecurity category until 2021 — five years after Cyberpion’s founding. We’ve got a head start and we are expanding the gap – with Connective Intelligence, we provide ever wider coverage of the evolving IT and threat landscape then overlay critical context and intelligence to eliminate noise and sharpen cybersecurity teams’ focus – so they can go on the offensive to proactively remediate the most urgent and critical risks, faster.
Don’t make attackers your discovery engine, discover risks first with IONIX
As IONIX, we’ll continue to deliver the widest coverage, and sharpest focus:
- Eliminate attack vectors: The only solution that covers the 20% and growing number of exploitable risks stemming from the digital supply chain. That’s one in five of your organization’s exploitable risks — risks that you’re likely overlooking but are just as appealing to threat actors as your first-party assets.
- Continuously mapping your real attack surface: Giving you insight into your real attack surface, including not just your owned assets but also your 2nd-, 3rd-, 4th, and nth-degree connections and dependencies.
- More assets, less noise: Cutting out the noise by leveraging patented Connective Intelligence and machine learning to eliminate false positives, provide actions not issues, and prioritize threats that require immediate action.
If you’re ready to take control and sharpen your focus on the most urgent, critical threats, request discovery to see the risks hiding in your attack surface.