Navigating Zero-day Vulnerabilities: 7 Proactive Steps for Rapid Response

Emergency response to zero-days
Zero-day vulnerabilities require an emergency response, disrupting proactive security initiatives and placing additional pressure on security teams. Despite not being the primary focus of their daily responsibilities, zero-days, especially those exploited in the wild, capture significant media attention. This often results in managers, executives, and even board members seeking immediate information about the company’s exposure to the latest threats.
The spotlight on zero-day vulnerabilities forces security teams to divert significant time and resources in effort to gather information, identify the scope of the exposure, and mitigate any risks. This scenario highlights the necessity for a proactive, structured approach to managing zero-day threats effectively, while minimizing unnecessary impact on your security team’s ongoing work.
Seven Proactive Steps in Zero-Day Response
Over the years, we’ve assembled the key seven steps that security teams should take to accelerate and streamline their response to an emerging zero-day threat. Based on these steps, we have expanded our attack surface management platform to help IONIX customers identify and manage zero-day exposures.
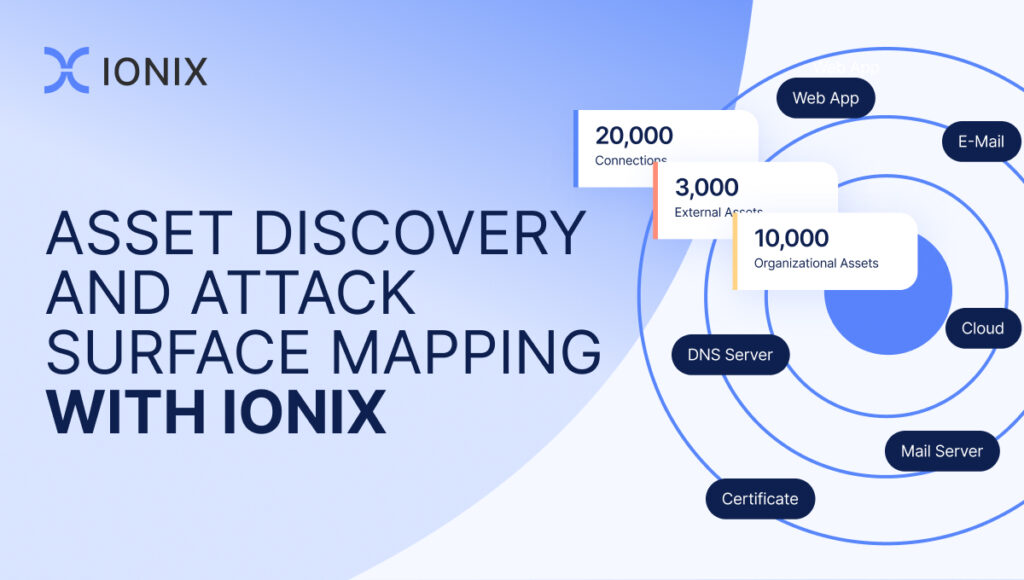
- Discovering your zero-day attack surface assets: The first step in assessing the potential impact of an emerging zero-day vulnerability is identifying all potentially vulnerable assets. This task can be challenging unless you use continuous attack surface discovery to map and monitor your organization.
- Mapping potential zero-day digital supply chain risks: In some cases, zero-day vulnerabilities in your connected digital supply chain assets (assets you do not manage directly) can pose a risk to your organizational assets. The recent MoveIT and the infamous Log4J vulnerabilities are such examples. In such cases, it is crucial to map these risks across your entire digital supply chain. Advanced attack surface management platforms like IONIX perform this task automatically as part of their attack surface discovery and assessment.
- Identifying vulnerable versions: Determining which assets are running the vulnerable versions of software will help you pinpoint the potentially vulnerable assets. In some cases, this information can be easily ascertained. In others, active tests can help make this determination. In either case, this information provides potentially vulnerable targets rather than actually exploitable ones.
- Validating Exposures: Beyond theoretical vulnerabilities, the focus shifts to validating exposures through exploitability testing. These active security tests determine exploitability; if and how a potential attacker could exploit the zero-day vulnerability.
- Prioritizing validated exposures: Not all vulnerabilities pose the same level of risk. Prioritizing validated exposures focuses security teams on the most urgent risks, ensuring that resources are allocated efficiently.
- Streamlining remediation with cross-team collaboration: Remediation is a multi-team process, where the heavy lifting is typically done by IT and devops teams. By prioritizing a small number of validated exposures, security teams can get the collaboration buy-in from their IT counterparts to ensure that remediation efforts are executed promptly and efficiently.
- Communicating with stakeholders: Keeping executives and IT teams informed is crucial during the zero-day response process. Clear, concise, and thorough updates help manage expectations and provide reassurance that the situation is being handled with the necessary expertise and attention.
Streamline and accelerate zero-day response with IONIX Threat Center
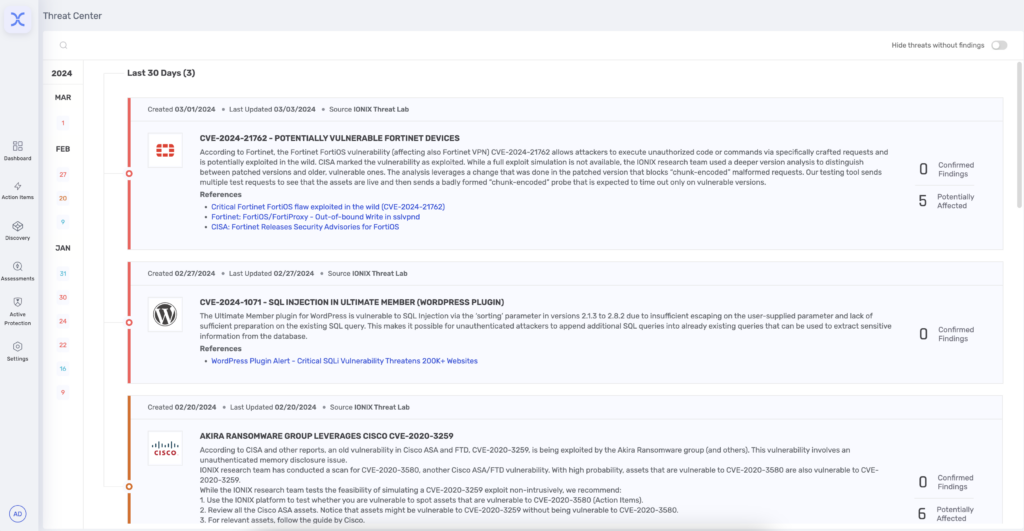
In an era where zero-day vulnerabilities can disrupt even the most well-prepared security strategies, IONIX Threat Center helps security teams streamline and accelerate response effectively. As part of IONIX’s comprehensive Attack Surface Management platform, the Threat Center equips security teams with the up-to-date view of their organizations zero-day attack surface, validated exposures, and actionable remediation strategies to tackle emerging vulnerabilities head-on.
IONIX Threat Center Highlights
The IONIX Threat Center provides access to information on new and emerging zero-day threats as they relate to the organization. This information allows security teams to quickly assess the relevance and potential impact of vulnerabilities as they are disclosed.
Comprehensive Attack Surface Discovery and Assessment
By conducting continuous attack surface discovery and risk assessment, IONIX ASM maps the complete inventory of internet-facing assets and their digital supply chains. Based on this inventory, the platform can immediately identify every asset that may be vulnerable to this new threat including organizational and digital supply chain assets.
Exploitability Testing for Accurate Exposure Validation
Beyond merely identifying potential vulnerabilities, IONIX employs sophisticated exploitability testing to validate whether and how a threat could be exploited in the organization’s unique environment. This targeted validation ensures that response efforts can be prioritized based on actual risk rather than theoretical exposure.
Expanding Exposure Validation Capabilities with the IONIX Threat Lab
The IONIX Threat Lab research team expands the Exposure Validation capabilities. New validation modules are created in these zero-day scenarios:
– Can be exploited by an external attacker
– Is already exploited in the wild
– Can be validated using non-intrusive exploitability test
Actionable Remediation Instructions and Seamless Workflow Integration
The IONIX Threat Center provides security teams with detailed information about the vulnerability itself, and clear visibility into validated exploitable and potentially exploitable risks. Zero results are displayed in cases to communicate that a scan was conducted, and no exploitable risk were found in reference to the specific zero-day.
One-click access from the validated risks provides a list of actionable remediation instructions enabling swift and effective action to mitigate risks. With seamless integration with existing security workflows and systems, IONIX can automatically dispatch these as tickets to relevant IT owners. This integration capability ensures that the transition from exposure detection to response is as smooth and efficient as possible, minimizing disruption to ongoing security operations.
Enhancing Stakeholder Communication with Automated Notifications
Recognizing the importance of clear and timely communication, the Threat Center provides automated notifications designed to streamline the flow of information to stakeholders, including executives and IT teams. This ensures that all parties are informed and aligned on the threat response process, facilitating quicker decision-making and response coordination.
Speed and Precision in Zero-Day Vulnerability Response
The IONIX Threat Center helps organizations to not only respond to zero-day vulnerabilities but to do so with speed and precision. By effectively exposing exploitable risks and streamlining zero-day response, the Threat Center significantly reduces the time and resources required to manage zero-day threats. Moreover, its actionable guidance and workflow integration ensures that security teams stay ahead of potential attackers.
To see the IONIX Threat Center in action, book your demo here.