How to Reduce Your Attack Surface (and Why It Matters)

Data breaches are an ever-present risk for organizations of all sizes — and the larger the attack surface, the greater the risk. Adopting best practices to reduce your attack surface is essential to mitigate these risks and protect your organization’s data integrity. There is growing awareness of the need to manage the attack surface, and reducing the attack surface is an essential component. However, many companies lack full visibility into their real attack surface, making reduction challenging. Further, the interconnected nature of IT assets means that even when businesses recognize the need to reduce the attack surface, they may lack the tools to do so effectively.
In this article, we’ll discuss the best ways to reduce your attack surface, why it’s vital to your company’s security, and how attack surface management makes it possible. Understanding how to reduce the attack surface is the first step towards fortifying your organization against cyber threats. So, first, let’s review what an attack surface is.
What is an Attack Surface?
Your company’s attack surface is the total of all attack vectors that hackers can use to gain access to your company’s network. So, what is an attack vector, you ask? An attack vector is essentially a method or pathway utilized by attackers to gain unauthorized access to a system, exploiting vulnerabilities to launch cyberattacks, steal data, or cause disruptions. These vectors can range from weak or compromised credentials, unpatched software, and cloud misconfigurations, to phishing, digital supply chain risks, and brute force attacks.
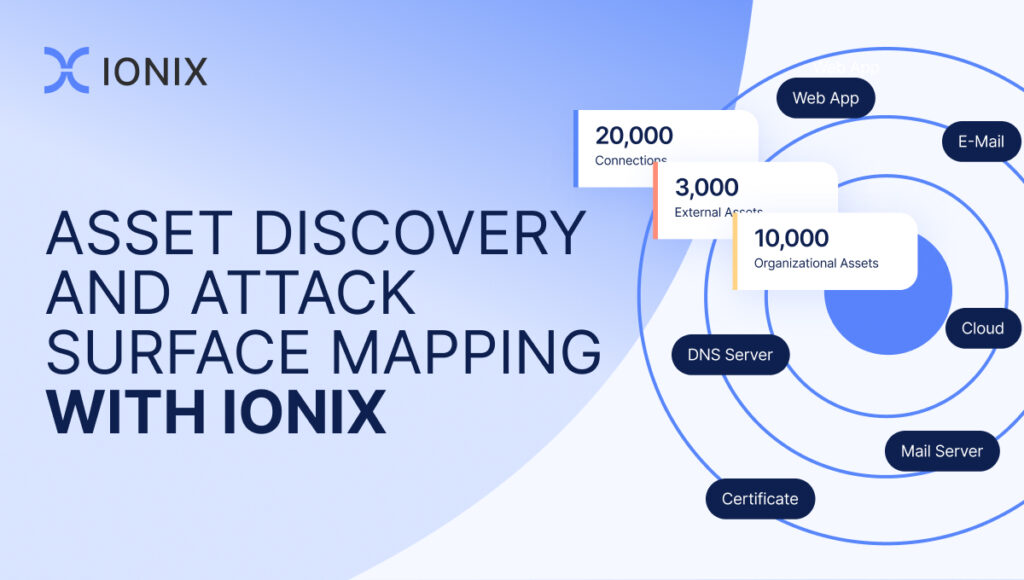
The digital attack surface spans across known internet-facing assets, hidden or unmanaged ones, often referred to as shadow IT, to dormant or forgotten assets, sometimes called Zombie IT.
Why the real attack surface is even bigger
Your real attack surface isn’t limited to owned assets; it also includes dependencies and connections that make up the digital supply chain. Internet facing attack surface discovery goes a step further by scrutinizing the security of digital supply chain connections that could serve as conduits for cyber threats. Threat actors are simply looking for a vulnerability that provides an attack vector, whether that means attacking an internet-facing asset directly or exploiting an exposed digital supply chain connection. In fact, 20% of exploitable attack surface risks now originate in the digital supply chain. As enterprises rely more on third-party vendors and services, digital supply chain risks will present and ever-growing challenge.
Why is It Important to Reduce Your Attack Surface?
Today’s large attack surfaces are challenging for security teams to manage. The larger the attack surface, the greater the potential for attack vectors and the greater the risk of an exploit.
The costs of a cyber attack are significant. According to IBM’s 2022 Cost of a Data Breach report, the global average cost of a data breach is $4.35 million. That can include mitigation and remediation costs, regulatory fines, costs associated with breach notifications and providing credit monitoring services to impacted consumers, legal costs, lost income resulting from business interruption, extortion paid to recover data after a ransomware attack, and public relations and reputation management costs.
Cyber attacks result in more than just financial costs. Business interruption and reputation damage diminish consumer trust in your organization and can turn potential investors, partners, and vendors away. Additionally, third-party vendors may be reluctant to re-establish connections prolonging disruption to business well after the attack has been contained and the risks remediated.
Attack Surface Reduction Begins with Visibility
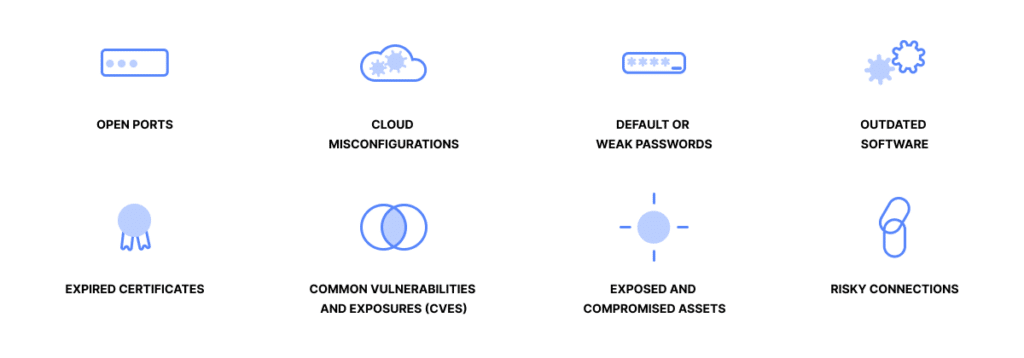
To initiate attack surface reduction, begin by mapping out your attack surface and digital supply chain. A strategic approach to decrease attack surface areas involves a thorough analysis of both digital and physical components of your organization’s network. Adopt a continuous internet facing asset discovery approach to uncover unfamiliar assets, shadow IT, and Zombie IT. Evaluate each asset meticulously to pinpoint risks, such as:
The attack surface is always changing as more vendors and services connect via the digital supply chain. For example, an employee may use a new service, data may be migrated to a different cloud server, or an existing third-party service might reconfigure its infrastructure. All of these activities change the attack surface and can potentially introduce new attack vectors, and your security team may not be aware that these changes occurred. That’s why attack surface mapping isn’t a one-time activity but an ongoing process to continuously monitor the attack surface risk.
Embracing a mindset of continuous attack surface discovery is crucial for maintaining up-to-date visibility. This means not only identifying new assets as they are added but also reassessing existing ones for changes in vulnerabilities and threat exposures. A robust reduction strategy must include a mechanism for ongoing risk analysis, ensuring that as your business grows, your security measures scale accordingly.
How to Reduce Your Attack Surface
To reduce attack surface, you have two primary approaches: reduce attack surface risk and reduce attack surface assets. Both approaches are vital for effective attack surface reduction.
1. Minimize attack surface risk
Let’s explore effective strategies on how to reduce attack surface risks. The goal is to minimize vulnerabilities and potential entry points for attackers by focusing on risk management and mitigation.
Maintain Complete Visibility
Achieving comprehensive visibility into the attack surface involves identify all digital environments and their assets on-premises, across public clouds, and on partners’ and vendors’ infrastructure.. This visibility is crucial for detecting vulnerabilities and forms the basis for further risk identification and prioritization.
Note that maintaining this visibility is not a static task but a dynamic process that adapts as new assets are added and as existing assets evolve. Thus it’s imperative to implement continuous monitoring to keep pace with these changes, ensuring that your visibility into the attack surface remains clear and comprehensive.
Identify and Prioritize Potential Attack Vectors
This step focuses on evaluating vulnerabilities to determine which pose the greatest risk. Considerations including exposure validation, threat intelligence data, and breach impact should be used to effectively prioritize risks. This strategy allows security teams to allocate their attention and resources towards mitigating the most severe vulnerabilities.
The prioritization of risks is an exercise in resource optimization. By categorizing vulnerabilities based on their severity, potential impact, and exploitability, security teams can create a structured response plan. This plan should guide immediate actions for high-priority risks while scheduling less critical issues for routine maintenance.
Eliminate High-Risk Attack Vectors and Continuous Monitoring
Implementing proactive security measures, such as adopting a Zero Trust model, enforcing strong encryption policies, and segmenting the network, can significantly reduce the likelihood of successful attacks. Continuous monitoring through regular vulnerability assessments and penetration testing is essential for early detection of new risks.
Automate to Minimize the Attack Surface
The use of automation is crucial in streamlining your bid to minimize the attack surface. Automated tools can perform regular scans, track changes in the network configuration, and even simulate attack scenarios to test the resilience of your systems. By automating these tasks, your security team is freed to focus on strategic analysis and proactive defense measures.
2. Reducing Attack Surface Assets
This strategy for attack surface reduction focuses on identifying and retiring assets that are no longer in use..
Decommission Zombie IT
Identifying and decommissioning Zombie IT—outdated, unused, or forgotten assets that remain connected to the organization’s network—is a highly effective attack surface reduction approach. These assets can pose significant security risks as they are often unmonitored, unpatched, and vulnerable to exploitation. The process begins with the discovery and inventory of all IT assets and identifying which assets are active, necessary, and compliant with current security standards, and which are not. Once identified, unnecessary or outdated assets should be systematically decommissioned.
Each decommissioned asset shrinks the attack surface, making it more manageable and less susceptible to breaches. The decommissioning process should be thorough, ensuring that all dependencies are accounted for and that the removal of one asset does not inadvertently expose new vulnerabilities.
Streamline Operations and Improve Security Posture
The process of decommissioning Zombie IT not only helps you reduce attack surface but also optimizes resource allocation. Ensuring that all data stored on these assets is securely backed up or migrated before decommissioning helps prevent business disruption. Proper decommissioning leads to better IT asset management, streamlined operations, and an improved overall security posture.
It’s important to note though that assets vary in significance and vulnerability. Some hold critical business data or support essential services, making them high-value targets for attackers. This understanding informs security protocols, ensuring that the most stringent measures are applied where they are most needed.
Parting thoughts
Reducing attack surface risk in today’s complex IT environments requires up-to-date visibility into known and unknown assets. It requires ongoing analysis and prioritization of risk, and actionable remediation steps. It also includes identification of Zombie IT that should be decommissioned. These requirements are outside the scope of traditional security tools like vulnerability management.
What you need is attack surface management. Attack surface management solutions can automate a lot of your workflows including dynamically mapping your entire attack surface, neutralizing some of the most exploitable risks, continuously monitoring your company’s assets to identify markers of misuse, and much more. Utilizing these solutions is a proactive measure to decrease attack surface vulnerabilities and enhance your cybersecurity framework.
What you don’t want though are irrelevant alerts and false positives. An attack surface management solution like IONIX assesses and prioritizes risks and — rather than bombarding your team with alerts — provides clear action items to keep your team laser-focused on the risks that matter. With IONIX, a single action item can resolve multiple issues, providing a significantly streamlined workflow aligned with the way your security operations team actually works. Book a demo today to learn how IONIX’s attack surface management solution provides ongoing public facing asset discovery and actionable remediation steps.