Gartner CTEM Starts with EASM
External Attack Surface Management (EASM) has emerged as a cybersecurity gold standard – a core component of modern cybersecurity programs. As digital organizations have grown more complex, getting the whole picture of the external attack surface – what’s connected to what and how this could pose danger – is a maze that only-world-class EASM solutions have been able to successfully navigate.
And this is why Gartner continues to position EASM as a primary use case of Gartner’s Continuous Threat Exposure Management (CTEM) framework. EASM, it seems, is even more pivotal than most cybersecurity stakeholders may have recognized. In this post, we’ll look at exactly what makes EASM foundational to Threat Exposure Management programs.
What is EASM?
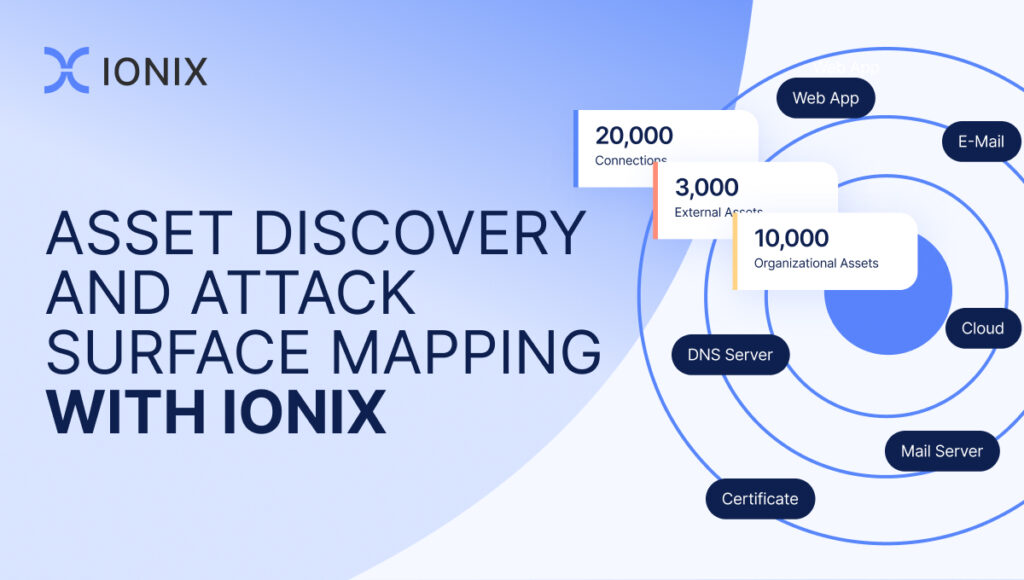
Just to get our terminology straight – an organization’s ‘external attack surface’ is the sum of its internet-facing assets and the associated attack vectors which can be exploited during an attack. This includes anything from domain names, SSL certificates and protocols to operating systems, servers, IOT devices and network services – both those under the direct control of the organization and those connected via the digital supply chain.
External Attack Surface Management (EASM) is the continuous discovery, monitoring, evaluation, prioritization, and remediation of these attack vectors – prioritized according to the actual risk posed by a given threat.
What is CTEM?
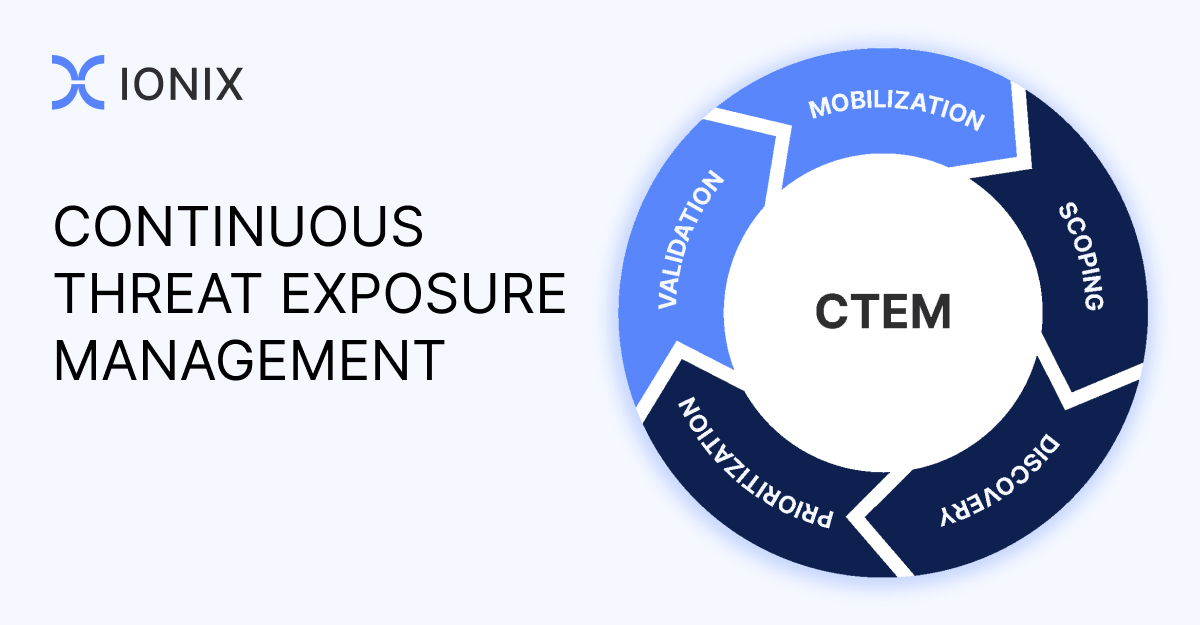
Continuous Threat Exposure Management (CTEM) is a framework designed to continuously surface, actively prioritize risks, and mobilize the defense of the biggest threats to your business. It’s a program, though, and not a tool.
Gartner introduced CTEM in 2022. Since then, putting this framework into action has become a priority across many organizations. The reason? CTEM is now considered one of the most effective methodologies to continuously reduce exposures.
“By 2026, organizations that prioritize their security investments based on a continuous exposure management program will be 3x less likely to suffer a breach”
Gartner
The simple goal of the CTEM framework is to lower the likelihood of weaknesses being exploited through a five-stage approach:
- Scoping
- Discovery
- Prioritization
- Validation
- Mobilization
While few dispute the power and validity of the CTEM framework, choosing a solution to best implement the principles of CTEM has been an issue many organizations have grappled with. In the following section we’ll review the rational for starting a Threat Exposure Management (TEM) program with EASM.
How Does EASM Fit into CTEM?
External Attack Surface Management (EASM) is a foundational use case for implementing Continuous Threat Exposure Management (CTEM). Here’s why:
Clear scope with significant impact
EASM focuses on an organization’s external facing assets. This provides a focused scope, making it more manageable for organizations to start their CTEM journey. In addition, managing the external attack surface is crucial, since it is the primary entry point for many cyber threats.
Visibility from the attacker’s perspective
EASM provides insights into how an attacker views the organization from the outside. By understanding and managing the external attack surface, organizations can proactively address vulnerabilities and misconfigurations before they are exploited by threat actors.
Growing ecosystem of tools
The EASM domain has seen a surge in specialized tools and solutions that help organizations identify, assess, and manage their external assets. This growing ecosystem makes it easier for organizations to adopt EASM as an initial step in their CTEM program.
Faster time to value
EASM tools operate from the outside, in a non-intrusive way. They continuously discover and expose risks across organizations’ internet facing assets and their digital supply chains. By proactively reducing their external attack surface, security teams can quickly demonstrate the value of the CTEM program to stakeholders. This can help in securing buy-in for further expansion and investment in the program.
Foundational for further expansion
EASM helps organization break security silos by providing a holistic view across hybrid on-premises and cross-cloud IT environments. Starting with EASM allows organizations to establish foundational processes, workflows, and collaboration mechanisms. Once these are in place, it becomes easier to expand the CTEM program to include other areas.
Aligns with digital transformation
As organizations increasingly adopt cloud services, online platforms, and digital interfaces for their operations, the external attack surface becomes even more critical. EASM aligns with digital transformation trends, ensuring that as organizations evolve, they have the security controls needed to continuously evolve their security posture.
The bottom line
By adopting EASM as the first use case for CTEM, companies take an important step on the road to realizing CTEM’s full potential. Advanced platforms, like IONIX ASM, that provide critical insights into attacker perspectives, fast time to value and alignment with digital transformation are just some of the reasons that Gartner found EASM to be a practical starting point that sets the stage for a more comprehensive CTEM strategy.