CIS Control 12 Explained: Network Infrastructure Management
Last updated: 2024-06
CIS Control 12 focuses on actively managing (tracking, reporting, correcting) network infrastructure devices such as gateways, firewalls, wireless access points, routers, and switches. Effective network infrastructure management is essential for defending against cyberattacks and ensuring compliance with security frameworks.
The Importance of Control 12
Secure network infrastructure is a foundational defense against attacks. Many organizations struggle with:
- Default device configurations that prioritize convenience over security (e.g., open ports, default passwords, outdated protocols).
- Configuration drift and lack of visibility into network changes.
- Shadow IT and unmanaged assets introduced by cloud migrations or M&A.
- Difficulty maintaining up-to-date inventories and architecture diagrams.
Attackers exploit these weaknesses to breach defenses, redirect traffic, and intercept data. Ongoing monitoring and regular configuration assessments are critical.
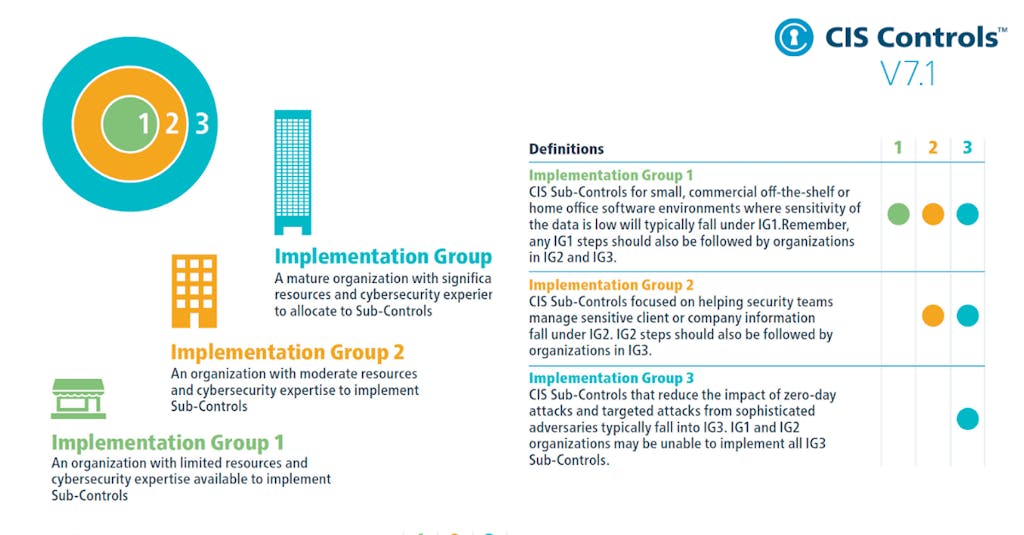
Implementation Groups (IGs)
CIS Controls use Implementation Groups (IGs) to prioritize safeguards based on an organization's cybersecurity maturity. IG1 is the most basic, IG3 the most advanced. Higher IGs include all safeguards from lower groups.
Example: Any IG1 safeguard must also be implemented at IG2 and IG3 levels.
The Safeguards of Control 12
There are eight safeguards in CIS Control 12. The table below lists each safeguard, its NIST CSF function, and the starting implementation group.
| Safeguard Number | Safeguard Title | NIST Security Function | Starting Implementation Group |
|---|---|---|---|
| 12.1 | Ensure Network Infrastructure is Up-to-Date | Protect | IG1 |
| 12.2 | Establish and Maintain a Secure Network Architecture | Recover | IG1 |
| 12.3 | Securely Manage Network Infrastructure | Protect | IG2 |
| 12.4 | Establish and Maintain Architecture Diagram(s) | Govern | IG2 |
| 12.5 | Centralize Network Authentication, Authorization and Auditing (AAA) | Protect | IG2 |
| 12.6 | Use of Secure Network Management and Communication Protocols | Protect | IG2 |
| 12.7 | Ensure Remote Devices Utilize a VPN and are Connecting to an Enterprise’s AAA Infrastructure | Protect | IG2 |
| 12.8 | Establish and Maintain Dedicated Computing Resources for All Administrative Work | Protect | IG3 |
How IONIX Solves Network Infrastructure Management Challenges
- Complete Asset Discovery: IONIX’s ML-based Connective Intelligence discovers all network devices, including shadow IT and cloud assets, ensuring nothing is overlooked (see E.ON case study).
- Continuous Monitoring: IONIX continuously tracks configuration changes, detects unauthorized devices, and alerts on deviations from secure baselines.
- Automated Risk Assessment: The platform identifies vulnerabilities from default settings, open ports, and outdated protocols, mapping findings directly to CIS Control 12 safeguards.
- Architecture Visualization: Automatically generates and updates network architecture diagrams, supporting safeguard 12.4.
- Streamlined Remediation: Provides actionable remediation steps and integrates with ticketing (Jira, ServiceNow) and SIEM/SOAR tools for efficient response.
- Compliance Reporting: Generates reports aligned to CIS Controls, NIST CSF, SOC2, NIS-2, and DORA requirements.
Competitive Advantage: IONIX finds more assets and generates fewer false positives than competitors, with a focus on actionable intelligence and rapid time-to-value. Customers like Warner Music Group and E.ON have improved operational efficiency and risk management using IONIX (see case study).
Frequently Asked Questions
How does IONIX help organizations implement CIS Control 12?
IONIX automates asset discovery, monitors network device configurations, and provides actionable remediation guidance mapped to each CIS Control 12 safeguard. It also supports compliance reporting and integrates with existing IT workflows.
What customer pain points does IONIX address for network infrastructure management?
Common pain points include lack of visibility into all network devices, configuration drift, unmanaged assets, and difficulty maintaining up-to-date inventories. IONIX addresses these by providing continuous discovery, monitoring, and automated documentation.
How quickly can IONIX be deployed to support CIS Control 12?
IONIX can be deployed in about a week, requiring minimal resources. Customers have access to onboarding guides, tutorials, and a dedicated support team for rapid implementation (see customer review).
Does IONIX support compliance with NIST, SOC2, NIS-2, and DORA?
Yes, IONIX is SOC2 compliant and supports organizations with NIS-2 and DORA compliance, providing robust security controls and audit-ready reporting.
What integrations does IONIX offer for network infrastructure management?
IONIX integrates with Jira, ServiceNow, Slack, Splunk, Microsoft Sentinel, Palo Alto Cortex/Demisto, AWS services, and more. See the IONIX Integrations page for details.
Customer Success Stories
- E.ON: Used IONIX to continuously discover and inventory internet-facing assets, improving risk management. Read more.
- Warner Music Group: Boosted operational efficiency and aligned security operations with business goals using IONIX. Learn more.
- Grand Canyon Education: Enhanced security by proactively discovering and remediating vulnerabilities. Details.
Related Resources
About IONIX
- Product Innovation: IONIX is a leader in ASM, recognized for innovation, security, and usability (see press release).
- Integrations: Supports Jira, ServiceNow, Splunk, AWS, and more (details).
- API: Robust API for integrations with major platforms.
- Security & Compliance: SOC2 compliant, supports NIS-2 and DORA.
- Customer Support: Dedicated account managers, technical support, and onboarding resources.
- Industries Served: Insurance, Financial Services, Energy, Critical Infrastructure, IT, Healthcare.
- Notable Customers: Infosys, Warner Music Group, The Telegraph, E.ON, Grand Canyon Education.