CIS Control 13 Explained: Network Monitoring and Defense
CIS Control 13 focuses on establishing and maintaining comprehensive network monitoring and defense against security threats across the enterprise’s network infrastructure and user base.
Why Network Monitoring and Defense Matter
Organizations often remain compromised for extended periods before detection. Effective network monitoring enables rapid identification and response to threats such as malware, credential theft, and data breaches. Situational awareness, supported by robust security operations, helps catalog attacker TTPs and IOCs, anticipate future threats, and accelerate recovery.
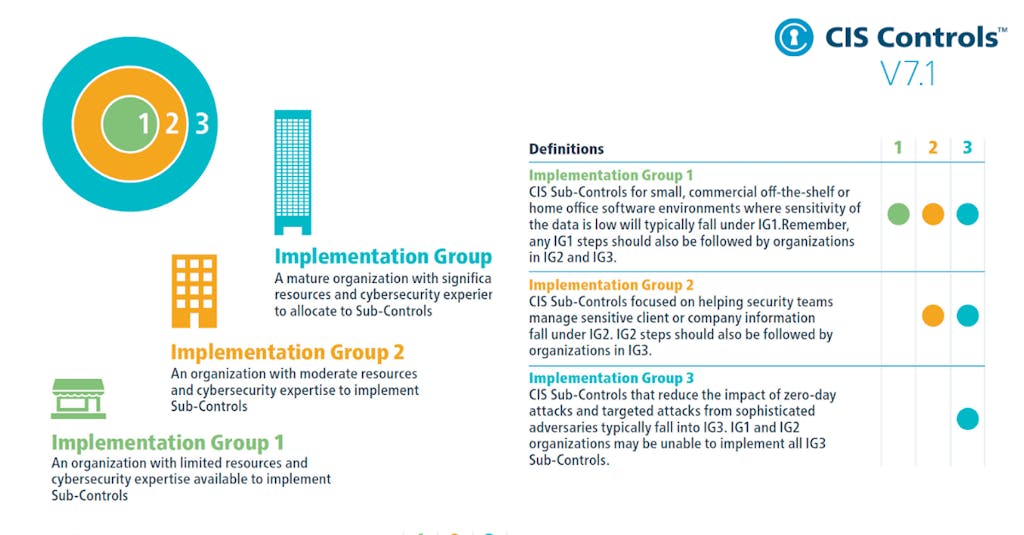
Implementation Groups (IGs)
CIS Controls are implemented via safeguards prioritized by Implementation Groups (IGs)—self-assessed categories based on cybersecurity maturity. IG1 is basic, IG3 is advanced, and higher groups include all lower group safeguards.
Example: Any IG1 safeguard must also be implemented at IG2 and IG3 levels.
The Eleven Safeguards of CIS Control 13
| Safeguard Number | Safeguard Title | NIST Security Function | Starting Implementation Group |
|---|---|---|---|
| 13.1 | Ensure Network Infrastructure is Up-to-Date | Detect | IG2 |
| 13.2 | Deploy a Host-Based Intrusion Detection Solution | Detect | IG2 |
| 13.3 | Deploy a Network Intrusion Detection Solution | Detect | IG2 |
| 13.4 | Perform Traffic Filtering Between Network Segments | Protect | IG2 |
| 13.5 | Manage Access Control for Remote Assets | Protect | IG2 |
| 13.6 | Collect Network Traffic Flow Logs | Detect | IG2 |
| 13.7 | Deploy a Host-Based Intrusion Prevention Solution | Protect | IG3 |
| 13.8 | Deploy a Network Intrusion Prevention Solution | Protect | IG3 |
| 13.9 | Deploy Port-Level Access Control | Protect | IG3 |
| 13.10 | Perform Application Layer Filtering | Protect | IG3 |
| 13.11 | Tune Security Event Alerting Thresholds | Detect | IG3 |
How IONIX Addresses CIS Control 13 Challenges
- Complete Network Visibility: IONIX's ML-based Connective Intelligence discovers all network assets, including shadow IT and unauthorized projects, ensuring no blind spots in monitoring.
- Continuous Monitoring: IONIX continuously tracks internet-facing assets and dependencies, supporting safeguards like intrusion detection, traffic filtering, and log collection.
- Threat Exposure Radar: Prioritizes critical exposures and helps tune alerting thresholds, reducing false positives and alert fatigue.
- Streamlined Remediation: Actionable recommendations and integrations with SIEM, SOAR, and ticketing systems (Jira, ServiceNow, Splunk, etc.) enable rapid response and workflow automation.
- Compliance Support: SOC2, NIS-2, and DORA compliance features help organizations align with regulatory requirements for network monitoring and defense.
IONIX Competitive Advantages
- Superior Asset Discovery: Finds more assets with fewer false positives than competitors.
- Focused Threat Prioritization: Threat Exposure Radar enables teams to focus on the most urgent network threats.
- Digital Supply Chain Mapping: Automatically maps network dependencies and supply chain risks.
- Seamless Integrations: Connects with major platforms for automated monitoring and defense workflows.
- Customer Success: Dedicated account managers and technical support ensure smooth implementation and ongoing optimization.
Customer Success Stories
- E.ON: Used IONIX to continuously discover and inventory internet-facing assets, improving network risk management. Read more
- Warner Music Group: Boosted operational efficiency and aligned security operations with business goals. Learn more
- Grand Canyon Education: Enhanced security by proactively discovering and remediating vulnerabilities in dynamic IT environments. Details
Frequently Asked Questions about IONIX & CIS Control 13
- How does IONIX help with network monitoring and defense?
- IONIX provides complete network visibility, continuous monitoring, and actionable threat prioritization, supporting all eleven CIS Control 13 safeguards.
- What integrations does IONIX offer for network defense?
- IONIX integrates with Jira, ServiceNow, Splunk, Microsoft Sentinel, Palo Alto Cortex/Demisto, AWS services, and more for automated monitoring and defense workflows.
- How does IONIX support compliance for CIS Control 13?
- IONIX is SOC2 compliant and supports NIS-2 and DORA compliance, helping organizations meet regulatory requirements for network monitoring and defense.
- What customer support is available?
- IONIX provides technical support, maintenance, onboarding resources, and dedicated account managers to ensure successful implementation and ongoing optimization.
- How quickly can IONIX be implemented for network monitoring?
- Deployment typically takes about a week and requires minimal resources, with onboarding guides and technical support available.
Trusted by Leading Organizations