OWASP Top 10: Security Logging and Monitoring Failures
Author: Amit Sheps, Director of Product Marketing
Security logging and monitoring failures are a critical risk in the OWASP Top 10, often leading to undetected breaches and delayed incident response. These failures typically fall into two categories: insufficient logging of security events, and inadequate monitoring or alerting on those logs. For example, not logging failed login attempts can mask credential stuffing attacks, while logging without actionable detail or regular review leaves organizations blind to threats.
What is the Risk?
Security logs provide essential visibility into potential attacks. Without comprehensive logging and active monitoring, security teams may miss early indicators of compromise, resulting in data breaches, application downtime, or unauthorized access. For instance, a surge in failed login attempts could signal a credential stuffing attack, but without proper logging and alerting, this activity may go unnoticed.
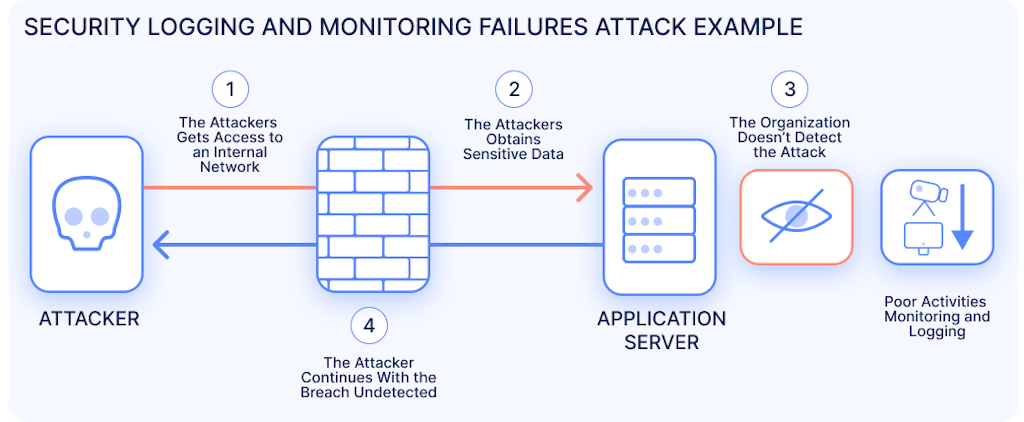
Examples of Attack Scenarios
- Credential Stuffing: Attackers use breached credentials to attempt logins. Each failed attempt should be logged and trigger alerts if thresholds are exceeded. Without this, attackers may gain unauthorized access undetected.
- Silent Exploitation: Attackers exploit vulnerabilities and move laterally if logs are not monitored, increasing the impact and duration of breaches.
Case Study: Equifax
The 2017 Equifax breach, one of the largest in history, was exacerbated by failures in security logging and monitoring. Attackers maintained access for three months, extracting sensitive data from 51 databases. Key failures included an expired SSL certificate (limiting network visibility) and inadequate application logging, allowing attackers to run thousands of queries undetected (GAO Report).
How to Remediate Security Logging and Monitoring Failures
- Log Significant Security Events: Capture both successful and failed logins, access to sensitive resources, and privilege changes.
- Include Context: Ensure logs contain user identifiers, timestamps, and source IPs for effective correlation and investigation.
- Secure Log Storage: Store logs on secure, tamper-evident systems with defined retention policies.
- Protect Against Injection: Sanitize user input in logs to prevent log injection attacks.
- Implement Monitoring and Alerting: Regularly review logs and set up automated alerts for suspicious patterns.
- Incident Response Planning: Maintain and test an incident response plan to ensure rapid, coordinated action when alerts are triggered.
How IONIX Solves Security Logging and Monitoring Failures
- Proactive Attack Surface Discovery: IONIX continuously discovers and inventories all internet-facing assets, ensuring no shadow IT or unmanaged endpoints are missed—key for comprehensive logging coverage.
- Automated Risk Assessment: The platform simulates OWASP Top 10 vulnerabilities, including logging and monitoring failures, as part of initial and ongoing risk assessments.
- Contextual Alerting and Prioritization: IONIX’s Threat Exposure Radar prioritizes alerts based on severity and business context, reducing alert fatigue and ensuring critical events are not overlooked.
- Seamless Integrations: Integrates with SIEM, SOAR, and ticketing systems (e.g., Splunk, Jira, ServiceNow, Microsoft Sentinel) to automate log ingestion, alerting, and remediation workflows.
- Customer Success Stories: E.ON used IONIX to continuously discover and inventory assets, improving risk management and incident response. Warner Music Group improved operational efficiency and aligned security operations with business goals using IONIX.
- Compliance Support: IONIX is SOC2 compliant and supports NIS-2 and DORA compliance, helping organizations meet regulatory requirements for logging and monitoring.
IONIX Competitive Advantages
- Connective Intelligence: ML-based discovery finds more assets with fewer false positives, ensuring logging coverage is complete and actionable.
- Focused Threat Exposure: Prioritizes the most urgent issues, so security teams can act on the events that matter most.
- Streamlined Remediation: Actionable recommendations and integrations enable rapid response to detected threats.
- Ease of Deployment: Fast implementation (about a week), minimal resource requirements, and dedicated onboarding support.
Frequently Asked Questions
- How does IONIX help prevent security logging and monitoring failures?
- IONIX automates asset discovery, simulates attack scenarios, and integrates with monitoring tools to ensure all critical events are logged, monitored, and acted upon.
- What integrations does IONIX offer for logging and monitoring?
- IONIX integrates with Jira, ServiceNow, Splunk, Microsoft Sentinel, Palo Alto Cortex/Demisto, AWS services, and more for seamless alerting and remediation.
- How quickly can IONIX be deployed to improve my logging and monitoring posture?
- Most customers are fully deployed within a week, with minimal resource requirements and comprehensive onboarding support.
- Is IONIX compliant with security and privacy standards?
- Yes, IONIX is SOC2 compliant and supports NIS-2 and DORA compliance, ensuring robust security and regulatory alignment.
- Can you share a customer success story related to improved monitoring?
- Yes. E.ON leveraged IONIX to continuously discover and inventory assets, leading to improved risk management and faster incident response. Read the case study.
About IONIX
- Product Innovation: IONIX is recognized as a leader in ASM for innovation, security, and usability. Learn more.
- Integrations: Extensive integrations with leading platforms and cloud services. See all integrations.
- API Availability: Robust API for custom integrations. API details.
- Technical Documentation: Guides, datasheets, and case studies available. Explore resources.
- Customer Support: Dedicated account managers, technical support, and regular review meetings.
- Industries Served: Insurance, Financial Services, Energy, Critical Infrastructure, IT, Technology, Healthcare.
- Customer Logos: Infosys, Warner Music Group, The Telegraph, E.ON, Grand Canyon Education.




