OWASP Top 10: Security Misconfiguration Vulnerabilities
Most applications have a range of settings that a user can configure. This may include implementing various security controls, turning features on and off, or creating accounts and access controls. Security misconfiguration vulnerabilities exist when an application is deployed in an insecure state. This could involve security features being disabled, running unnecessary functions, or leaving default accounts and passwords in place.
In this article
What is the Risk?
Often, security and usability are somewhat at odds with one another because security controls add friction to the user experience. For example, it would be far easier if no web application required authentication; however, this would leave user accounts vulnerable to attack.
If necessary security controls aren’t implemented or are disabled, an attacker can exploit an application in various ways. Potential impacts include data breaches, Denial of Service (DoS) attacks, or misuse of an application’s functionality.
Examples of Attack Scenarios
Security misconfigurations are a broad class of vulnerabilities that fall much later in the Software Development Lifecycle (SDLC) than the rest of the OWASP Top Ten. Most OWASP vulnerabilities deal with design or implementation errors by the developers, while security misconfigurations are errors related to an application’s deployment. Since this vulnerability class covers every way that a user can misconfigure an application in a way that undermines its security, there are numerous ways that an attacker can exploit this error.
Some examples include the following:
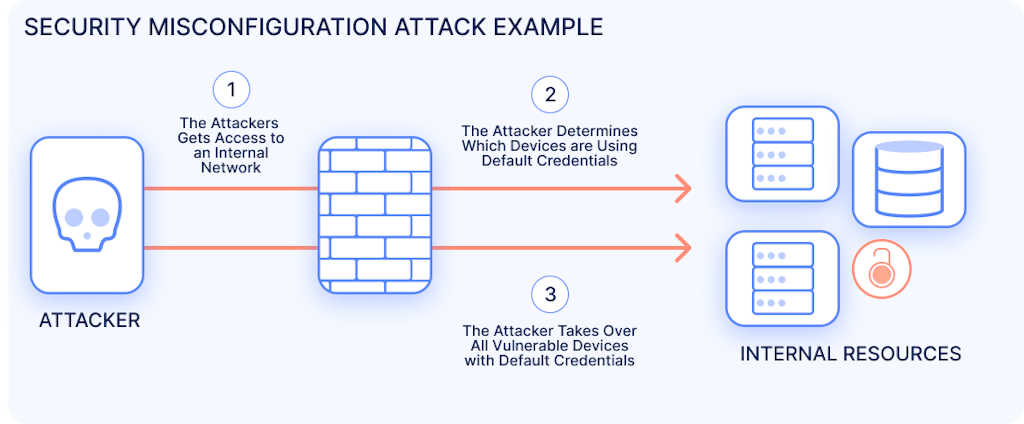
Account Takeover Attacks
Several types of security misconfigurations relate to access management. For example, an application could be deployed with the default account enabled with its password unchanged. Alternatively, a user may fail to implement proper access controls or disable authentication security options such as multi-factor authentication (MFA).
In these scenarios, an attacker could gain authenticated access to the system by logging in with the default credentials or guessing the user’s password. Now, they have access to the user’s account, which may contain sensitive functionality or be able to access restricted functionality.
Vulnerability Exploitation
A web application may be designed to offer a range of features to its users, but a particular company may not need all of these capabilities. However, they leave the unused functionality enabled within the application.
This is dangerous because these unused features expand an organization’s digital attack surface and may contain unpatched vulnerabilities that an attacker could exploit. If the organization isn’t using a particular feature, it may not keep it properly up-to-date or be aware that it’s under attack. This could provide an attacker with a foothold on the organization’s network or lead to the exposure of sensitive information.
Sensitive Data Leakage
Web applications and web servers have various potential vectors for data leakage. For example, allowing directory listing on a web server could allow an attacker to map the filesystem and download sensitive files. Alternatively, the error messages generated by a web application or web server may contain excessive and sensitive information.
These data leaks can be valuable to an attacker performing reconnaissance against the organization’s environment. The ability to download application code might reveal exploitable vulnerabilities or hardcoded credentials. Overly verbose error messages could provide hints regarding the organization’s web infrastructure and potential attack vectors that the attacker could use to exploit it.
Case Study: Microsoft Power Apps
In 2021, it was discovered that Microsoft Power Apps, a low-code development platform, had insecure default settings that left user data exposed. By default, the platform’s API permitted public access to data stored by web and mobile apps created using the platform.
The popularity of the platform meant that over 1,000 web apps were impacted by the incident, including both private companies and government agencies, and an estimated 38 million user records were exposed across the tool’s customer base. This included highly sensitive information, such as Social Security Numbers (SSNs) and COVID-19 vaccination status.
How to Remediate Security Misconfiguration Vulnerabilities
Security misconfigurations can be caused by various factors, and some best practices to help avoid these errors include the following:
- Define Hardening Processes: Applications and systems are rarely shipped in a hardened and secure state by default. Having processes in place to disable default accounts, implement access controls, and implement other necessary security controls can reduce the risk of oversights and errors.
- Disable Unnecessary Features: Each application and feature in an organization’s environment expands its digital attack surface. Disabling anything that isn’t necessary or used by the business reduces the risk of exploitation.
- Implement Segmentation: Segmentation breaks an organization’s environment into isolated sections, making it more difficult for an attacker to move through the network. Implementing segmentation at the network level or via access controls reduces the risk associated with security misconfigurations.
- Automate Configuration Management: Software may be misconfigured from the start or have its configurations drift over time. Automated configuration management monitors for insecure settings, enabling the security team to take action regarding potential threats.
How IONIX Can Help
While security misconfigurations cover a wide range of potential vulnerabilities, some errors are more common than others. For example, the use of default accounts and a failure to patch systems with known vulnerabilities are common mistakes. Attackers know this and look for these types of errors in their attacks.
IONIX helps organizations to manage the risk of security misconfigurations and other OWASP Top Ten vulnerabilities via proactive attack simulation. When performing a risk assessment, the IONIX platform checks for common errors in this vulnerability class and reports the results to the security team. For more information on how your organization can better manage its digital attack surface with IONIX, reach out for a demo.



